2021/January Latest Braindump2go 350-401 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 350-401 Real Exam Questions!
QUESTION 264
Refer to the exhibit. What does the snippet of code achieve?
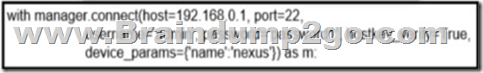
A. It creates a temporary connection to a Cisco Nexus device and retrieves a token to be used for API calls.
B. It opens a tunnel and encapsulates the login information, if the host key is correct.
C. It opens an ncclient connection to a Cisco Nexus device and maintains it for the duration of the context.
D. It creates an SSH connection using the SSH key that is stored, and the password is ignored.
Answer: C
Explanation:
ncclient is a Python library that facilitates client-side scripting and application development around the NETCONF protocol.
The above Python snippet uses the ncclient to connect and establish a NETCONF session to a Nexus device (which is also a NETCONF server).
QUESTION 265
Refer to the exhibit. Both controllers are in the same mobility group. Which result occurs when client 1 roams between APs that are registered to different controllers in the same WLAN?
![image_thumb[15] image_thumb[15]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb15_thumb.png)
A. Client 1 contact controller B by using an EoIP tunnel.
B. CAPWAP tunnel is created between controller A and controller B.
C. Client 1 users an EoIP tunnel to contact controller A.
D. The client database entry moves from controller A to controller B.
Answer: D
Explanation:
This is called Inter Controller-L2 Roaming. Inter-Controller (normally layer 2) roaming occurs when a client roam between two APs registered to two different controllers, where each controller has an interface in the client subnet. In this instance, controllers exchange mobility control messages (over UDP port 16666) and the client database entry is moved from the original controller to the new controller.
QUESTION 266
Which two sources cause interference for Wi-Fi networks? (Choose two).
A. mirrored wall
B. 900MHz baby monitor
C. fish tank
D. DECT 6.0 cordless
E. Incandesent lights
Answer: AC
Explanation:
Windows can actually block your WiFi signal. How? Because the signals will be reflected by the glass.
Some new windows have transparent films that can block certain wave types, and this can make it harder for your WiFi signal to pass through. Tinted glass is another problem for the same reasons. They sometimes contain metallic films that can completely block out your signal. Mirrors, like windows, can reflect your signal. They`re also a source of electromagnetic interference because of their metal backings.
Reference: https://dis-dot-dat.net/what-materials-can-block-a-wifi-signal/
An incandescent light bulb, incandescent lamp or incandescent light globe is an electric light with a wire filament heated until it glows. WiFi operates in the gigahertz microwave band. The FCC has strict regulations on RFI (radio frequency interference) from all sorts of things, including light bulbs -> Incandesent lights do not interfere Wi-Fi networks.
Note:
+ Many baby monitors operate at 900MHz and won`t interfere with Wi-Fi, which uses the 2.4GHz band.
+ DECT cordless phone 6.0 is designed to eliminate wifi interference by operating on a different frequency. There is essentially no such thing as DECT wifi interference.
QUESTION 267
Refer to the exhibit. What are two effects of this configuration? (Choose two.)
![image_thumb[2] image_thumb[2]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb2_thumb.png)
A. R1 becomes the active router.
B. R1 becomes the standby router.
C. If R2 goes down, R1 becomes active but reverts to standby when R2 comes back online.
D. If R1 goes down. R2 becomes active and remains the active device when R1 comes back online.
E. If R1 goes down, R2 becomes active but reverts to standby when R1 comes back online.
Answer: AD
QUESTION 268
Refer to the exhibit. After an engineer configures an EtherChannel between switch SW1 and switch SW2, this error message is logged on switch SW2.
![image_thumb[3] image_thumb[3]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb3_thumb.png)
Based on the output from SW1 and the log message received on Switch SW2, what action should the engineer take to resolve this issue?
A. Configure the same protocol on the EtherChannel on switch SW1 and SW2.
B. Connect the configuration error on interface Gi0/1 on switch SW1.
C. Define the correct port members on the EtherChannel on switch SW1.
D. Correct the configuration error on interface Gi0/0 switch SW1.
Answer: A
Explanation:
In this case, we are using your EtherChannel without a negotiation protocol. As a result, if the opposite switch is not also configured for EtherChannel operation on the respective ports, there is a danger of a switching loop. The EtherChannel Misconfiguration Guard tries to prevent that loop from occuring by disabling all the ports bundled in the EtherChannel.
QUESTION 269
Which deployment option of Cisco NQFW provides scalability?
A. clustering
B. Inline tap
C. high availability
D. tap
Answer: C
QUESTION 270
Refer to the exhibit. An engineer must ensure that all traffic entering AS 200 from AS 100 chooses Link 2 as an entry point. Assume that all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers.
Which configuration accomplishes this task?
![image_thumb[4] image_thumb[4]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb4_thumb.png)
A. R3(config)#route-map PREPEND permit 10
R3(config-route-map)#set as-path prepend 200 200 200
R3(config)#router bgp 200
R3#(config-router)#neighbor 10.1.1.1 route-map PREPEND out
B. R4(config)#route-map PREPEND permit 10
R4(config-route-map)#set as-path prepend 100 100 100
R4(config)#router bgp 200
R4(config-router)#neighbor 10.2.2.2 route-map PREPEND in
C. R4(config)#route-map PREPEND permit 10
R4(config-route-map)#set as-path prepend 200 200 200
R4(config)#router bgp 200
R4(config-router)#neighbor 10.2.2.2 route-map PREPEND out
D. R3(config)#route-map PREPEND permit 10
R3(config-route-map)#set as-path prepend 100 100 100
R3(config)#router bgp 200
R3(config-router)#neighbor 10.1.1.1 route-map PREPEND in
Answer: A
QUESTION 271
What are two differences between the RIB and the FIB? (Choose two.)
A. The FIB is derived from the data plane, and the RIB is derived from the FIB.
B. The RIB is a database of routing prefixes, and the FIB is the Information used to choose the egress interface for each packet.
C. FIB is a database of routing prefixes, and the RIB is the information used to choose the egress interface for each packet.
D. The FIB is derived from the control plane, and the RIB is derived from the FIB.
E. The RIB is derived from the control plane, and the FIB is derived from the RIB.
Answer: BE
Explanation:
The Forwarding Information Base (FIB) contains destination reachability information as well as next hop information. This information is then used by the router to make forwarding decisions. The FIB allows for very efficient and easy lookups.
QUESTION 272
Refer to the exhibit. Which command set must be added to the configuration to analyze 50 packets out of every 100?
![image_thumb[8] image_thumb[8]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb8_thumb.png)
![image_thumb[9] image_thumb[9]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb9_thumb.png)
A. Option A
B. Option B
C. Option C
D. Option D
Answer: C
QUESTION 273
Using the EIRP formula, what parameter is subtracted to determine the EIRP value?
A. transmitter power
B. antenna cable loss
C. antenna gain
D. signal-to-noise ratio
Answer: B
Explanation:
Once you know the complete combination of transmitter power level, the length of cable, and the antenna gain, you can figure out the actual power level that will be radiated from the antenna. This is known as the effective isotropic radiated power (EIRP), measured in dBm.
EIRP is a very important parameter because it is regulated by governmental agencies in most countries. In those cases, a system cannot radiate signals higher than a maximum allowable EIRP. To find the EIRP of a system, simply add the transmitter power level to the antenna gain and subtract the cable loss.
QUESTION 274
What is the purpose of the LISP routing and addressing architecture?
A. It creates two entries for each network node, one for Its identity and another for its location on the network.
B. It allows LISP to be applied as a network visualization overlay though encapsulation.
C. It allows multiple Instances of a routing table to co-exist within the same router.
D. It creates head-end replication used to deliver broadcast and multicast frames to the entire network.
Answer: A
Explanation:
Locator ID Separation Protocol (LISP) solves this issue by separating the location and identity of a device through the Routing locator (RLOC) and Endpoint identifier (EID):
+ Endpoint identifiers (EIDs) ?assigned to end hosts.
+ Routing locators (RLOCs) ?assigned to devices (primarily routers) that make up the global routing system.
QUESTION 275
How does the EIGRP metric differ from the OSPF metric?
A. The EIGRP metric is calculated based on bandwidth only. The OSPF metric is calculated on delay only.
B. The EIGRP metric is calculated based on delay only. The OSPF metric is calculated on bandwidth and delay.
C. The EIGRP metric Is calculated based on bandwidth and delay. The OSPF metric is calculated on bandwidth only.
D. The EIGRP metric Is calculated based on hop count and bandwidth. The OSPF metric is calculated on bandwidth and delay.
Answer: C
Explanation:
By default, EIGRP metric is calculated:
metric = bandwidth + delay
While OSPF is calculated by:
OSPF metric = Reference bandwidth / Interface bandwidth in bps (Or Cisco uses 100Mbps (108) bandwidth as reference bandwidth. With this bandwidth, our equation would be:
Cost = 108/interface bandwidth in bps)
QUESTION 276
Refer to the exhibit. The traceroute fails from R1 to R3. What is the cause of the failure?
![image_thumb[10] image_thumb[10]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb10_thumb.png)
A. The loopback on R3 Is in a shutdown stale.
B. An ACL applied Inbound on loopback0 of R2 Is dropping the traffic.
C. An ACL applied Inbound on fa0/1 of R3 is dropping the traffic.
D. Redistribution of connected routes into OSPF is not configured.
Answer: C
Explanation:
We see in the traceroute result the packet could reach 10.99.69.5 (on R2) but it could not go any further so we can deduce an ACL on R3 was blocking it. Note: Record option displays the address(es) of the hops (up to nine) the packet goes through.
QUESTION 277
What is used to validate the authenticity of the client and is sent in HTTP requests as a JSON object?
A. SSH
B. HTTPS
C. JVVT
D. TLS
Answer: B
Explanation:
https://developer.atlassian.com/server/crowd/json-requests-and-responses/
QUESTION 278
Which method does Cisco DNA Center use to allow management of non-Cisco devices through southbound protocols?
A. It creates device packs through the use of an SDK
B. It uses an API call to interrogate the devices and register the returned data.
C. It obtains MIBs from each vendor that details the APIs available.
D. It imports available APIs for the non-Cisco device in a CSV format.
Answer: A
Explanation:
Cisco DNA Center allows customers to manage their non-Cisco devices through the use of a Software Development Kit (SDK) that can be used to create Device Packages for third-party devices.
Reference: https://developer.cisco.com/docs/dna-center/#!cisco-dna-center-platform-overview/multivendor-support-southbound
QUESTION 279
An engineer is configuring GigabitEthernet1/0/0 for VRRP. When the router has the highest priority In group 5, It must assume the master role.
Which command set should the engineer add to the configuration to accomplish this task?
![image_thumb[13] image_thumb[13]](http://examgod.com/bdimages/2021-January-NewQ264-Q285_D2FC/image_thumb13_thumb.png)
A. Option A
B. Option B
C. Option C
D. Option D
Answer: B
QUESTION 280
In a Cisco SD-Access wireless architecture, which device manages endpoint ID to Edge Node bindings?
A. fabric control plane node
B. fabric wireless controller
C. fabric border node
D. fabric edge node.
Answer: A
Explanation:
SD-Access Wireless Architecture Control Plane Node – A Closer Look Fabric Control-Plane Node is based on a LISP Map Server / Resolver Runs the LISP Endpoint ID Database to provide overlay reachability information + A simple Host Database, that tracks Endpoint ID to Edge Node bindings (RLOCs) + Host Database supports multiple types of Endpoint ID (EID), such as IPv4 /32, IPv6 /128* or MAC/48 + Receives prefix registrations from Edge Nodes for wired clients, and from Fabric mode WLCs for wireless clients + Resolves lookup requests from FE to locate Endpoints + Updates Fabric Edge nodes, Border nodes with wireless client mobility and RLOC information
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/latam/docs/2018/pdf/BRKEWN-2020.pdf
QUESTION 281
What is the responsibility of a secondary WLC?
A. It shares the traffic load of the LAPs with the primary controller.
B. It avoids congestion on the primary controller by sharing the registration load on the LAPs.
C. It registers the LAPs if the primary controller fails.
D. It enables Layer 2 and Layer 3 roaming between Itself and the primary controller.
Answer: C
Explanation:
When the primary controller (WLC-1) goes down, the APs automatically get registered with the secondary controller (WLC-2). The APs register back to the primary controller when the primary controller comes back on line. Reference: https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/69639-wlc-failover.html
QUESTION 282
Which control plane protocol is used between Cisco SD-WAN routers and vSmart controllers?
A. TCP
B. OMP
C. UDP
D. BGP
Answer: B
Explanation:
Cisco SD-WAN uses Overlay Management Protocol (OMP) which manages the overlay network. OMP runs between the vSmart controllers and WAN Edge routers (and among vSmarts themselves) where control plane information, such as the routing, policy, and management information, is exchanged over a secure connection.
QUESTION 283
In a Cisco Catalyst switch equipped with two supervisor modules an administrator must temporally remove the active supervisor from the chassis to perform hardware maintenance on it. Which mechanism ensure that the active supervisor removal is not disruptive to the network operation?
A. NSF/NSR
B. SSO
C. HSRP
D. VRRP
Answer: B
Explanation:
Stateful Switchover (SSO) provides protection for network edge devices with dual Route Processors (RPs) that represent a single point of failure in the network design, and where an outage might result in loss of service for customers.
Reference: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SY/configuration/guide/sy_swcg/stateful_switchover.html
QUESTION 284
Which deployment option of Cisco NGFW provides scalability?
A. tap
B. inline tap
C. high availability
D. clustering
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/firepower/fxos/clustering/asa- cluster-solution.html
Clustering lets you group multiple Firepower Threat Defense (FTD) units together as a single logical device. Clustering is only supported for the FTD device on the Firepower 9300 and the Firepower 4100 series. A cluster provides all the convenience of a single device (management, integration into a network) while achieving the increased throughput and redundancy of multiple devices.
QUESTION 285
In a Cisco SD-Access fabric, which control plane protocol is used for mapping and resolving endpoints?
A. DHCP
B. VXLAN
C. SXP
D. LISP
Answer: D
Explanation:
![]()
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/cisco-sda-design-guide.html
Resources From:
1.2020 Latest Braindump2go 350-401 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-401.html
2.2020 Latest Braindump2go 350-401 PDF and 350-401 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1EIsykNTrKvqjDVs9JMySv052qbrCpe8V?usp=sharing
3.2020 Free Braindump2go 350-401 PDF Download:
https://www.braindump2go.com/free-online-pdf/350-401-PDF(275-286).pdf
https://www.braindump2go.com/free-online-pdf/350-401-PDF-Dumps(264-274).pdf
https://www.braindump2go.com/free-online-pdf/350-401-VCE(287-298).pdf
https://www.braindump2go.com/free-online-pdf/350-401-VCE-Dumps(299-307).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!