May/2021 Latest Braidump2go CS0-002 Exam Dumps with PDF and VCE Free Updated Today! Following are some new CS0-002 Real Exam Questions!
QUESTION 611
A financial institution’s business unit plans to deploy a new technology in a manner that violates existing information security standards. Which of the following actions should the Chief Information Security Officer (CISO) take to manage any type of violation?
A. Enforce the existing security standards and controls
B. Perform a risk analysis and qualify the risk with legal
C. Perform research and propose a better technology
D. Enforce the standard permits
Answer: B
QUESTION 612
An analyst is reviewing the following code output of a vulnerability scan:
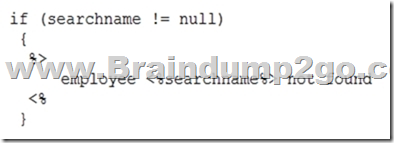
Which of the following types of vulnerabilities does this MOST likely represent?
A. A XSS vulnerability
B. An HTTP response split vulnerability
C. A credential bypass vulnerability
D. A carriage-return, line-feed vulnerability
Answer: C
QUESTION 613
The threat intelligence department recently learned of an advanced persistent threat that is leveraging a new strain of malware, exploiting a system router. The company currently uses the same device mentioned in the threat report. Which of the following configuration changes would BEST improve the organization’s security posture?
A. Implement an IPS rule that contains content for the malware variant and patch the routers to protect against the vulnerability
B. Implement an IDS rule that contains the IP addresses from the advanced persistent threat and patch the routers to protect against the vulnerability
C. Implement an IPS rule that contains the IP addresses from the advanced persistent threat and patch the routers to protect against the vulnerability
D. Implement an IDS rule that contains content for the malware variant and patch the routers to protect against the vulnerability
Answer: A
QUESTION 614
A company’s senior human resources administrator left for another position, and the assistant administrator was promoted into the senior position. On the official start day, the new senior administrator planned to ask for extended access permissions but noticed the permissions were automatically granted on that day. Which of the following describes the access management policy in place at the company?
A. Mandatory-based
B. Host-based
C. Federated access
D. Role-based
Answer: D
QUESTION 615
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year. Below is the incident register for the organization:
![image_thumb[1] image_thumb[1]](http://examgod.com/bdimages/May-2021Q611-Q635_E92F/image_thumb1_thumb.png)
Which of the following should the organization consider investing in FIRST due to the potential impact of availability?
A. Hire a managed service provider to help with vulnerability management
B. Build a warm site in case of system outages
C. Invest in a failover and redundant system, as necessary
D. Hire additional staff for the IT department to assist with vulnerability management and log review
Answer: C
QUESTION 616
A security analyst reviews a recent network capture and notices encrypted inbound traffic on TCP port 465 was coming into the company’s network from a database server. Which of the following will the security analyst MOST likely identify as the reason for the traffic on this port?
A. The traffic is common static data that Windows servers send to Microsoft
B. Someone has configured an unauthorized SMTP application over SSL
C. A connection from the database to the web front end is communicating on the port
D. The server is receiving a secure connection using the new TLS 1.3 standard
Answer: B
QUESTION 617
A threat intelligence analyst has received multiple reports that are suspected to be about the same advanced persistent threat. To which of the following steps in the intelligence cycle would this map?
A. Dissemination
B. Analysis
C. Feedback
D. Requirements
E. Collection
Answer: E
QUESTION 618
During an incident investigation, a security analyst acquired a malicious file that was used as a backdoor but was not detected by the antivirus application. After performing a reverse-engineering procedure, the analyst found that part of the code was obfuscated to avoid signature detection. Which of the following types of instructions should the analyst use to understand how the malware was obfuscated and to help deobfuscate it?
A. MOV
B. ADD
C. XOR
D. SUB
E. MOVL
Answer: C
QUESTION 619
An organization has several systems that require specific logons. Over the past few months, the security analyst has noticed numerous failed logon attempts followed by password resets. Which of the following should the analyst do to reduce the occurrence of legitimate failed logons and password resets?
A. Use SSO across all applications
B. Perform a manual privilege review
C. Adjust the current monitoring and logging rules
D. Implement multifactor authentication
Answer: A
QUESTION 620
An application server runs slowly and then triggers a high CPU alert. After investigating, a security analyst finds an unauthorized program is running on the server. The analyst reviews the application log below.
![image_thumb[2] image_thumb[2]](http://examgod.com/bdimages/May-2021Q611-Q635_E92F/image_thumb2_thumb.png)
Which of the following conclusions is supported by the application log?
A. An attacker was attempting to perform a DoS attack against the server
B. An attacker was attempting to download files via a remote command execution vulnerability
C. An attacker was attempting to perform a buffer overflow attack to execute a payload in memory
D. An attacker was attempting to perform an XSS attack via a vulnerable third-party library
Answer: C
QUESTION 621
A security analyst is attempting to utilize the following threat intelligence for developing detection capabilities:
APT X’s approach to a target would be sending a phishing email to the target after conducting active and passive reconnaissance. Upon successful compromise, APT X conducts internal reconnaissance and attempts to move laterally by utilizing existing resources. When APT X finds data that aligns to its objectives, it stages and then exfiltrates data sets in sizes that can range from 1GB to 5GB. APT X also establishes several backdoors to maintain a C2 presence in the environment.
In which of the following phases in this APT MOST likely to leave discoverable artifacts?
A. Data collection/exfiltration
B. Defensive evasion
C. Lateral movement
D. Reconnaissance
Answer: A
QUESTION 622
A security analyst is scanning the network to determine if a critical security patch was applied to all systems in an enterprise. The organization has a very low tolerance for risk when it comes to resource availability. Which of the following is the BEST approach for configuring and scheduling the scan?
A. Make sure the scan is credentialed, covers all hosts in the patch management system, and is scheduled during business hours so it can be terminated if it affects business operations.
B. Make sure the scan is uncredentialed, covers all hosts in the patch management system, and is scheduled during off-business hours so it has the least impact on operations.
C. Make sure the scan is credentialed, has the latest software and signature versions, covers all hosts in the patch management system, and is scheduled during off-business hours so it has the least impact on operations.
D. Make sure the scan is credentialed, uses a limited plugin set, scans all host IP addresses in the enterprise, and is scheduled during off-business hours so it has the least impact on operations.
Answer: D
QUESTION 623
A security analyst is probing a company’s public-facing servers for vulnerabilities and obtains the following output:
![image_thumb[4] image_thumb[4]](http://examgod.com/bdimages/May-2021Q611-Q635_E92F/image_thumb4_thumb.png)
Which of the following changes should the analyst recommend FIRST?
A. Implement File Transfer Protocol Secure on the upload server
B. Disable anonymous login on the web server
C. Configure firewall changes to close port 445 on 124.45.23.112
D. Apply a firewall rule to filter the number of requests per second on port 80 on 124.45.23.108
Answer: D
QUESTION 624
While reviewing log files, a security analyst uncovers a brute-force attack that is being performed against an external webmail portal. Which of the following would be BEST to prevent this type of attack from being successful?
A. Create a new rule in the IDS that triggers an alert on repeated login attempts
B. Implement MFA on the email portal using out-of-band code delivery
C. Alter the lockout policy to ensure users are permanently locked out after five attempts
D. Leverage password filters to prevent weak passwords on employee accounts from being exploited
E. Configure a WAF with brute-force protection rules in block mode
Answer: C
QUESTION 625
A security analyst reviews SIEM logs and detects a well-known malicious executable running in a Windows machine. The up-to-date antivirus cannot detect the malicious executable. Which of the following is the MOST likely cause of this issue?
A. The malware is fileless and exists only in physical memory
B. The malware detects and prevents its own execution in a virtual environment
C. The antivirus does not have the malware’s signature
D. The malware is being executed with administrative privileges
Answer: D
QUESTION 626
A security engineer is reviewing security products that identify malicious actions by users as part of a company’s insider threat program. Which of the following is the MOST appropriate product category for this purpose?
A. SCAP
B. SOAR
C. UEBA
D. WAF
Answer: B
QUESTION 627
A large organization wants to move account registration services to the cloud to benefit from faster processing and elasticity. Which of the following should be done FIRST to determine the potential risk to the organization?
A. Establish a recovery time objective and a recovery point objective for the systems being moved
B. Calculate the resource requirements for moving the systems to the cloud
C. Determine recovery priorities for the assets being moved to the cloud-based systems
D. Identify the business processes that will be migrated and the criticality of each one
E. Perform an inventory of the servers that will be moving and assign priority to each one
Answer: D
QUESTION 628
A security analyst is reviewing the following DNS logs as part of security-monitoring activities:
![image_thumb[5] image_thumb[5]](http://examgod.com/bdimages/May-2021Q611-Q635_E92F/image_thumb5_thumb.png)
Which of the following MOST likely occurred?
A. The attack used an algorithm to generate command and control information dynamically
B. The attack attempted to contact www.google.com to verify Internet connectivity
C. The attack used encryption to obfuscate the payload and bypass detection by an IDS
D. The attack caused an internal host to connect to a command and control server
Answer: D
QUESTION 629
A security analyst is required to stay current with the most recent threat data and intelligence reports. When gathering data, it is MOST important for the data to be:
A. proprietary and timely
B. proprietary and accurate
C. relevant and deep
D. relevant and accurate
Answer: D
QUESTION 630
An executive assistant wants to onboard a new cloud-based product to help with business analytics and dashboarding. Which of the following would be the BEST integration option for this service?
A. Manually log in to the service and upload data files on a regular basis
B. Have the internal development team script connectivity and file transfers to the new service
C. Create a dedicated SFTP site and schedule transfers to ensure file transport security
D. Utilize the cloud product’s API for supported and ongoing integrations
Answer: D
QUESTION 631
A security analyst received a series of antivirus alerts from a workstation segment, and users reported ransomware messages. During lessons-learned activities, the analyst determines the antivirus was able to alert to abnormal behavior but did not stop this newest variant of ransomware. Which of the following actions should be taken to BEST mitigate the effects of this type of threat in the future?
A. Enabling sandboxing technology
B. Purchasing cyber insurance
C. Enabling application blacklisting
D. Installing a firewall between the workstations and Internet
Answer: A
QUESTION 632
An organization used a third party to conduct a security audit and discovered several deficiencies in the cybersecurity program. The findings noted many external vulnerabilities that were not caught by the vulnerability scanning software, numerous weaknesses that allowed lateral movement, and gaps in monitoring that did not detect the activity of the auditors. Based on these findings, which of the following would be the BEST long-term enhancement to the security program?
A. Quarterly external penetration testing
B. Monthly tabletop scenarios
C. Red-team exercises
D. Audit exercises
Answer: D
QUESTION 633
A security analyst working in the SOC recently discovered instances in which hosts visited a specific set of domains and IPs and became infected with malware. Which of the following is the MOST appropriate action to take in this situation?
A. Implement an IPS signature for the malware and update the blacklisting for the associated domains and IPs
B. Implement an IPS signature for the malware and another signature request to block all the associated
domains and IPs
C. Implement a change request to the firewall setting to not allow traffic to and from the IPs and domains
D. Implement an IPS signature for the malware and a change request to the firewall setting to not allow traffic to and from the origin IPs subnets and second-level domains
Answer: D
QUESTION 634
The help desk notified a security analyst that emails from a new email server are not being sent out. The new email server was recently added to the existing ones. The analyst runs the following command on the new server:
![image_thumb[8] image_thumb[8]](http://examgod.com/bdimages/May-2021Q611-Q635_E92F/image_thumb8_thumb.png)
Given the output, which of the following should the security analyst check NEXT?
A. The DNS name of the new email server
B. The version of SPF that is being used
C. The IP address of the new email server
D. The DMARC policy
Answer: A
QUESTION 635
Which of the following should a database administrator implement to BEST protect data from an untrusted server administrator?
A. Data deidentification
B. Data encryption
C. Data masking
D. Data minimization
Answer: B
Resources From:
1.2021 Latest Braindump2go CS0-002 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/cs0-002.html
2.2021 Latest Braindump2go CS0-002 PDF and CS0-002 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1ijxiiJOyOJ7Z8VAogjAysf7iznDnjE46?usp=sharing
3.2021 Free Braindump2go CS0-002 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/CS0-002-VCE-Dumps(627-642).pdf
https://www.braindump2go.com/free-online-pdf/CS0-002-PDF-Dumps(611-626).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!